4 Frameworks and Concepts
4.1 Problem Analysis
Data scientists are inundated with questions and requests. A director in the Finance department shoots you this email in the morning:
Has the SaaS business been growing over the past three months and will the trend continue over the next quarter?
If this question hits the desk of the data science team, does everyone know what needs to be done? Is it clear what the question is? Is there a deeper question here that needs to be answered first?
Framing of a problem expresses the issue on behalf of those who are experiencing it, in a way that the team can develop a shared understanding (Church 2023). Without proper framing, the team cannot rally around the problem and develop a solution. Well-framed problems are expressed in a meaningful way and set the team up for success. Ill-framed problems have the opposite effect.
The question about the growth of the SaaS is not well framed. A better ask would have been:
Measured by net retention rate (NRR), what is the NRR over the past quarter and can you predict the NRR for the next quarter, assuming that we make no major changes to sales and marketing?
Two methodological approaches that help unpack a problem and get to its essence are The 5-Why framework and the 40-20-10-5 rule. This is known as root cause analysis.
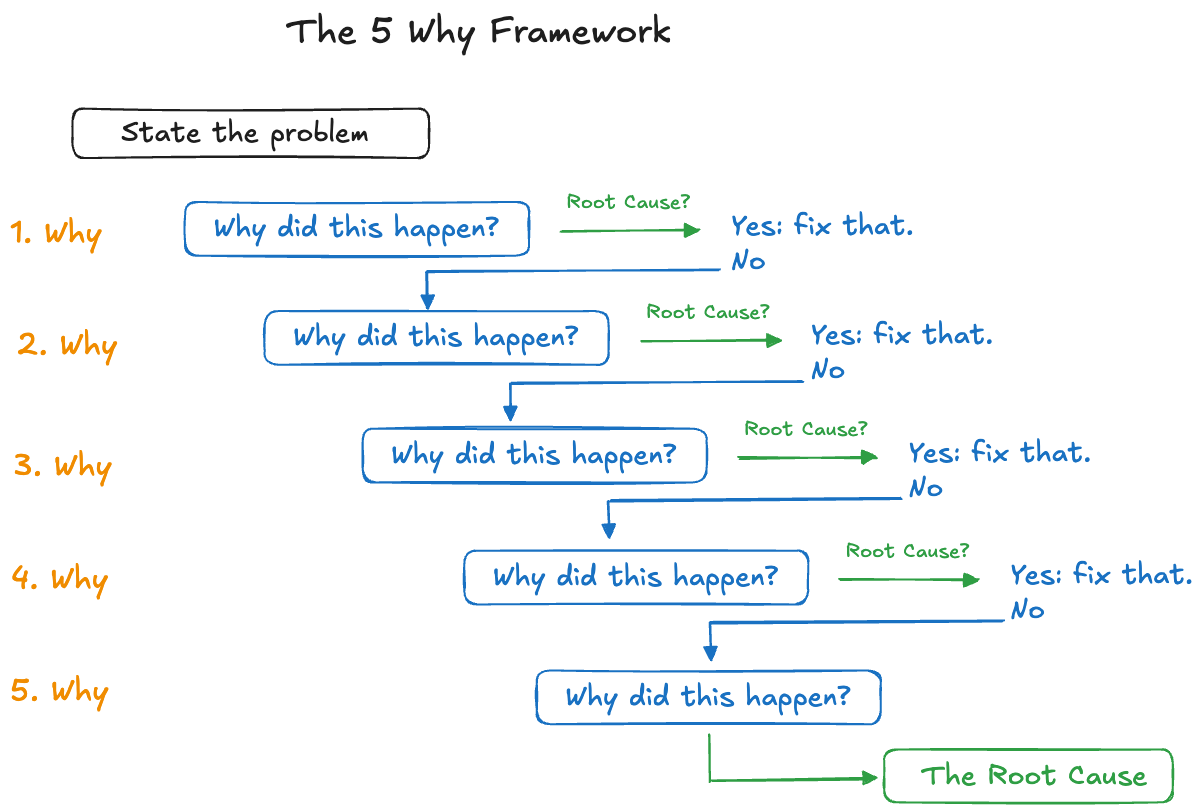
The 5 Whys
This framework was developed in the 1950s at Toyota to improve production quality and is still in use today. It works best for small and simple problems but you can try it on any problem. If it turns out that the causes for each Why create their own lines of inquiry, the 5-Why tool is too simple.
The idea is to state the problem and then ask repeatedly “Why did this happen?”, up to five times. At any point, the Why might reveal the root cause of the problem. If it does not, drill deeper and go to the next question (Figure 4.1).
The first Why should reveal the main problem, but is not necessarily the root cause of the problem. Any of the Why can reveal the root cause and you do not necessarily have to go down 5-deep.
Problem: The Website was not Updated in Time.
Why did this happen?
\(\Rightarrow\) The developers did not have the content they needed.Why did this happen?
\(\Rightarrow\) The copywriter did not provide the content.Why did this happen?
\(\Rightarrow\) The copywriter was waiting on approval from the VP Marketing.Why did this happen?
\(\Rightarrow\) The VP Marketing forgot to approve the content.Why did this happen?
\(\Rightarrow\) He was on a business trip.
Possible solutions:
- Make sure that approval authority is delegated prior to absences from office.
- Ensure that time for content approval is allocated during absences.
- Set up an automated approval process that moves a decision to next in line if the decision is not made within a certain time frame.
- Bump the decision to the Senior VP Marketing if the VP does not respond within a certain time. Bump the decision then to the Executive VP Marketing if the SVP does not respond within a certain time.
- Replace the VP of Marketing with someone who has better memory.
The framework is not useful if the responses are informed by personal biases and do not get to the heart of the issues. Preconceived notions about the causes can mislead the analysis as can reliance on guesses or assumptions. Being convinced that one has found the root cause can lead to superficial solutions.
Problem: The Application Crashed while Scoring a Model Online
Why did this happen?
\(\Rightarrow\) The code tried to access invalid memory when reading one of the variables needed in the scoring model.Why did this happen?
\(\Rightarrow\) No memory was allocated for the variable, instead, the application tried to read from a NULL pointer causing a segmentation violation.Why did this happen?
\(\Rightarrow\) No information was available for the particular variable, hence no memory was allocated.Why did this happen?
\(\Rightarrow\) The input form does not require a valid input, the user can leave it blank.
If you stop after the first Why the solution is to make sure memory is always valid, implying to allocate memory for all variables and to pre-populate it with default values, for example, NULLs or NaNs.
You would still have to make sure that the application can process NULL and NaN values. The same is true if you stop after the second Why.
Digging deeper we get to the reason for the absence of data. It seems that if the information is required, then the data intake form should make sure that a valid value is populated based on user input. The downstream checks for NULL/NaNs and sufficient memory allocation are good programming practice anyway but are not solving the root cause of the crash—they are resolving the symptoms of the crash.
The 5-Why procedure starts with formulating a short and specific problem or issue the team needs to address. It helps to have a facilitator, who is not a team member, to ask “Why did this happen?”. The team shoul make effort to confirm their responses with data where possible. You stop asking “Why did this happen?” when one of the following occurs:
- There is no new information.
- You get to the “Aha!” moment when the team realizes the root cause. For example, you get to “Oh no, I cannot believe we have been doing it that way all this time!”
- The reasons are outside the team’s control.
- The responses start to repeat.
The 40-20-10-5 Rule
This rule is related to the 5-why framework in that it is trying to get to the essence of a problem. The approach is different.
Rather than repeatedly asking why something happened, the 40-20-10-5 rule asks us to reframe the problem using fewer and fewer words. It is not that important whether you start with 40 or 80 words, what matters is to increasingly strip away stuff that does not matter. What you are left with is the essence of the problem. The root of the problem emerges as the number of words is reduced.
Problem: The Application Crashed while Scoring a Model Online
40-words: A segmentation violation occurred when the code scored a data record collected online that contained invalid data. Specifically, a NULL pointer was accessed instead of a memory address where memory was allocated to hold the user-supplied value for the variable.
20-words: When the application encounters a NULL pointer it crashes, this can be the result of not retrieving data and not setting defaults.
10-words: Missing user input results in memory not being allocated.
5-words: User did not provide data.
4.2 SUCCESs—Ideas That Stick
In their book Made To Stick, the brothers Chip and Dan Heath ask why some ideas stick and others die (Heath and Heath 2007). At the beginning of the book they contrast a passage from a document and a story.
Passage: Community Building
Comprehensive community building naturally lends itself to a return-on-investment rationale that can be modeled, drawing on existing practice. A factor constraining the flow of resources to CCIs is that funders must often resort to targeting or categorical requirements in grant making to ensure accountability.
Story: Kidney Heist (abbreviated)
Dave is a frequent business traveler. On a recent trip to Atlantic City he had time to kill after meeting with clients and before his flight home. He went to a local bar for a drink. He’d just finished one drink when an attractive woman approached and asked if she could buy him another. Sure, he said. The woman brought two drinks back from the bar, one for her and one for him. Dave took a sip and that was the last thing he remembered.
He woke up, disoriented, in a hotel bathtub filled with ice. He spotted a note along with a cell phone on a small table beside the bathtub: “DON’T MOVE. CALL 911”.
His fingers numb from the ice, he called 911. The operator seemed oddly familiar with his situation. She said “Sir, I want you to reach behind you, slowly and carefully. Is there a tube protruding from your lower back?”
Sure enough, there was a tube. The operator said “Sir, don’t panic, but there is a ring of organ thieves operating in this city; they harvested one of your kidneys. Paramedics are on their way.”
Suppose you had just read those texts for the first time and are asked to retell them tomorrow. Which passage or story would you be more likely to recount? Almost all of us would remember the kidney heist story, including many of its details: the bar, the drinks, the woman, the bathtub filled with ice water, the 911 operator. And of course, getting your kidney harvested. I say “almost all of us” because some might find the passage on community building more memorable—if that is you, then you are a rarity.
Heath and Heath (2007) develop a framework for gauging the stickiness of an idea. A sticky idea is one that is understood and remembered, and has a lasting impact by changing the audience’s opinions or behavior. The concept of the sticky idea translates directly to sticky communication.
In order for an idea to be sticky it does not have to be truthful. The kidney heist story is an urban legend. And it is a very sticky story. The story first appeared in 1991 and circulated widely for more than a decade, despite being debunked. For a fact check of the story and a hint of its possible origin, click here.
But wait, why do we need a framework for making our communications “stick”? We already know about storytelling principles, we know the goal of the communication, and we know the audience. Think of a biology school teacher who knows their audience, knows the material (cell mitosis), and is a very effective speaker. All the ingredients for a successful lecture on mitosis are there. The big question is about the message. How should the teacher communicate mitosis to the students?
The framework of the Heath brothers is about how to craft the core message and it rests on six principles:
Simplicity. The message must be simple, not in the sense of being dumbed down, but in the sense of being stripped down to its core, its essence.
Unexpectedness. To maintain audience interest when it takes time to get an idea across, we can stoke their curiosity by opening and closing gaps in their knowledge.
Concreteness. Convey the message in terms of human actions and sensory information with concrete images: the bathtub filled with ice. By communicating concrete messages, everyone will understand the message the same way.
Credibility. Sticky ideas carry their own credentials. The audience can see for themselves that the message is credible.
Emotions. To make people care about your idea, make them feel something. Tap into what the audience cares about. This might require work finding out what exactly your audience does care about. Heath and Heath (2007) give the example of teenagers these days not quitting smoking because of health consequences but because they resent the duplicity of tobacco companies.
Stories. Hearing stories prepares us to act on ideas. Stories make the message memorable.
In short, sticky ideas are Simple, Unexpected, Concrete, Credentialed, Emotional Stories (SUCCESs).
4.3 Brandolini’s Law
Albert Brandolini is an Italian software developer who coined in 2013 by way of a Twitter post a law that bears his name (Figure 4.2).
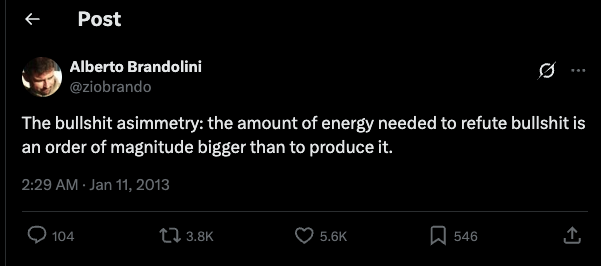
With slightly corrected grammar the law is also known as the bullshit asymmetry principle:
The amount of energy needed to refute bullshit is an order of magnitude bigger than that needed to produce it.
Example: MMR Autism Study in Lancet
Andrew Wakefield and twelve coauthors published in 1998 the paper “Ileal-lymphoid-nodular hyperplasia, non-specific colitis, and pervasive developmental disorder in children” in the reputable medical journal The Lancet. The paper claimed to establish cause and effect relationship between the MMR (measles, mumps, rubella) vaccine and colitis and between colitis and autism. This paper is the source of the imagined relationship between vaccines and autism.
The study caused a public stir and resulted in a decline in vaccinations, which in turn led to deadly measles outbreaks around the world.
Other researchers were not able to reproduce and confirm the paper’s findings. It was disclosed that Wakefield had a financial interest worth several million dollars per year selling test kits. In 2010 it was found that Wakefield had been dishonest in the research, that portions of the study were falsified, and that The Lancet had been deceived. The journal fully retracted the study, Wakefield recanted and lost his medical license.
It took 12 years of energy to refute the bullshit Wakefield produced in a single paper. Conspiracy theories about the connection between vaccines and autism are still swirling today. The U.S. Department of Health and Human Services hired in March 2025 vaccine critic David Greier, who holds no medical credentials, to conduct a study on the link of vaccines and autism—long after the link has been debunked.
It seems that we still need to spend more energy to refute the bullshit.
In 2020, researchers studied the sensitivity to bullshit and found that
people are more receptive to bullshit, and less sensitive to detecting bullshit, under conditions in which they possess relatively few self-regulatory resources.
4.4 Modes of Intelligence
Gardner (1983) coined the idea of multiple intelligences. Rather than a single, general intelligence, human intelligence is made up of different modalities (Figure 4.3). The modalities most associated with the traditional notion of general intelligence are the linguistic and the logical-mathematical intelligences.
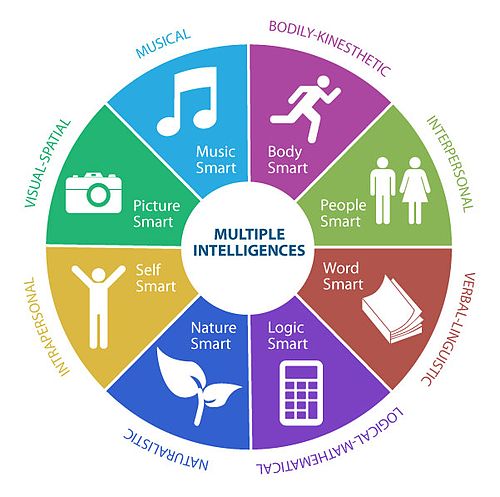
The intelligences (modalities) express themselves as skills or competencies. Someone with high linguistic intelligences learns languages easily and enjoys reading, writing, and storytelling. Someone with well-developed interpersonal intelligence will be able to sense other’s moods and intentions, they have high empathy.
Critics of the theory of multiple intelligences object to using the term intelligence to describe what they consider to be just abilities, talents, or aptitudes. The theory conflates personality, talent, and learning style and there is no experimental data to back up the categorization. Further, Gardner’s theory is based on low correlations between the modes of intelligence, as if they are almost orthogonal. The correlations between different aspects of intelligence are typically strong, however, supporting the idea of a general intelligence.
Despite the criticism, the theory of modes of intelligences is helpful to us in several ways.
It helps us to understand the abilities of others and how to adjust mode of communication for the benefit of the recipient. If you are communicating to people who work daily with maps (spatial intelligence), making your point by presenting text or tables adds extra cognitive burden.
It helps to recognize how different abilities are being used in solving data science problems. Except for the naturalistic and musical intelligences, you will likely be challenged as a data scientist to exercise all modes of intelligence. The diversity of thoughts and ways of looking at a problem is a strength of teams.
| Mode | Skills | Data Science Relevance |
|---|---|---|
| Verbal-Linguistic | Sensitivity to words and their meaning. Includes abstract reasoning and symbolic thinking. Learns languages easily; enjoys reading, writing, storytelling | Need to communicate quantitative information through language |
| Logical-Mathematical | Inductive and deductive reasoning. Recognizing patterns and relationships. Good at problem finding and convergent problem solving. | An essential part of research, discovering relationships, testing hypotheses. Application of abstract rules to specific problems. |
| Visual-Spatial | Mental visualization (seeing with the mind’s eye) and perception of the world. Practical problem solving and artistic creation. | Producing data visualizations and working in abstract, high-dimensional spaces. Design of applications and interfaces. |
| Interpersonal | Establish relationships with others. Sensitivity to other’s moods and intentions. Empathetic. Can be leaders or followers. | Cooperating with and leading others. Essential to working on teams. |
| Intrapersonal | Knowledge of self and ability to reflect and introspect. Predict and manage your own reaction. | Developing abstract theory. Leading and decision making in high-stress situations. |
| Body-Kinesthetic | Control of bodily movements and motor control. Includes sense of timing and sense of goal of physical action. Prefers hands-on learning. | Communicating data science knowledge to hands-on learners. Giving presentations. |
| Musical-Rhythmical | Sensitivity to sounds, rhythms, timber, meter, tones, and pitch. | |
| Naturalistic | Ability to recognize flora and fauna. Nurturing and relating information to one’s natural surroundings. Pattern recognition, taxonomy, and empathy for living beings are essential cognitive skills. | Clearly important in our past as hunters, gatherers, and farmers. Not of great relevance in working with data. |
4.5 Computational Kindness
The Principle
Computational kindness is a concept and principle introduced in Christian and Griffiths (2017). It asks us to consider the cognitive (computational) burden in interactions with others. This consideration is obviously relevant to how we communicate with others.
In designing functions and algorithms, computer scientists worry a great deal about computational complexity, the resources required to carry out a computational task. Particular attention is paid to the number of operations required (time complexity), the memory requirements (space complexity) or the amount of data exchanged over the network (communication complexity). For example, search algorithms are ranked in terms of their time complexity—using O-notation. The complexity of the best algorithm that solves a problem is the complexity of the problem.
The underlying idea is that computation should be minimized—computation is bad. It is bad to compute more than necessary, require more memory than necessary, communicate with other machines more than necessary. In other words, the underlying principle is to minimize the labor of thought, to minimize the computational burden.
This principle translates very well into how we make decisions and design systems in real life. You are computationally kind when you are respectful of the cognitive problems you force others to solve. Figure 4.4 shows digital signage at a bus stop that has a low cognitive burden; it is computationally kind. The arrival times, even if estimated, of the next six buses visiting the stop are shown in order.
If I am waiting for the Number 12 bus, and stopping at the coffee shop nearby takes 5 minutes, I can be assured that I will not miss the bus should I opt for a latte now. The cognitive burden of this sign is much lower than that of Figure 4.5.

As Christian and Griffiths (2017) put it,
We can be “computationally kind” to others by framing issues in terms that make the underlying computational problem easier.
Kind but not Polite
Computational kindness and politeness can be at odds.
Etiquette suggests to figure out how to spend the evening out by asking
“What do you want to do tonight?”
The question places the cognitive burden of the decision on the other party. That is called “passing the cognitive buck”. They now have to figure out your preferences unless you will go along with their decision or they do not care to consider your preferences. It is computationally more kind to constrain the problem presented to the other party. You can state your preferences—“I want to go to a movie”—or provide a limited set of options to choose from:
“Let’s go to McDonald’s or Taco Bell followed by either a movie or playing pool at the sports bar.”
Computational kindness reduces mental burden but can be detrimental to your relationships.
Why are folks more likely to schedule meetings when you ask
“Can you meet tomorrow at 10 am?”
instead of
“What days and times next week are convenient for you?”
The answer lies in the mental burden to craft a response. The first question specifies constraints of the solution space. Now I do not have to spend mental energy going through the open slots in my calendar, assemble a list of possible days and times for a meeting, send them back to the inquirer and wait for a response. All I have to do is check my calendar against a narrow constraint: tomorrow at 10 am. The first question is computationally kind, reducing mental burden by adding a constraint. Asking what days and times are convenient is computationally cruel.
The more polite response when someone tries to schedule with you is to say “I am flexible”. It is also the computationally most cruel one because it passes the buck of computation to the inquirer. They have to do all the work to narrow down the large number of possibilities. Saying “I can do Monday at 2 pm and Wednesday at 4 pm” is computationally kind because it constrains the requester to two options. And if neither of those work they will come back with another day and time—which you can likely accept because you are flexible.
Our brains are sophisticated computing machines. If we design algorithms to make the best use of resources, then we can also strive to make everyday tasks more computationally friendly to our brain. Opportunities are everywhere.
- Restaurant policies to secure a table have very different levels of mental labor. An open seating policy means whoever gets to an open table first gets to sit down. Customers will hover, constantly checking on which tables might open up, anxiously awaiting their turn. A policy where patron check-in upon arrival, can visit the bar, and are being told when their table opens up has a much lower cognitive burden for the patron, but is less computationally kind on the restaurant.
A reservation service that guarantees you a table has the lowest stress level for the patron and the highest computational burden for the restaurant. Unless the restaurant knows how to take a reservation but not how to hold a reservation.
Airline boarding policies. First-come-first serve versus assigned groups that board the plane from the back.
The bus stop that announces the arrival time of the buses versus one that makes you guess and wait.
Navigating a cluttered website with too much information and repeated ads versus a clean design where information is easy to find.
Assembly instructions that are written in some Klingon dialect.
Amazon’s 1-Click online buying system reduced the cognitive load of ordering online. With a shipping address and a credit card stored in the profile, you can check out the items in the shopping cart with a single click on the website.
Assignment: Designing a Parking Lot
You are operating a mall or large venue and are designing a parking lot for visitors of the space. Four designs are being proposed:
- A standard grid of lanes leading away from the venue with parking spaces on both sides of the lane.
- A standard multi-story parking deck.
- A single lane leading away from the venue with parking spaces on both sides of the lane.
- A helix-type structure that winds upward from the ground level where the venue is located. Parking spaces are accessed directly from the helix.
- Rank the four designs in terms of computational kindness to drivers.
- Are parking lot designs you find in real life paying attention to computational kindness considerations?
- Can you think of other designs or technologies that balance the tradeoff between mental labor of finding a parking spot and convenience?
In Communication
In communication we want to be computationally kind without being impolite. We want to minimize cognitive load for the communicator and the recipient of information—particularly for the latter. We want to reduce the mental effort required to receive communication and to respond to it.
The benefits are clearer and more engaging communication, better understanding and collaboration, less frustration, more trust and collaboration.
Here are some ways to be kind in communication:
Be mindful of how questions are asked. Avoid open-ended questions such as “What do you think?” or “Questions, comments, concerns?”. Instead ask specific questions such as “Is retention or revenue the main driver of the project?” Provide options to choose from.
Be mindful of the recipient’s understanding. Avoid jargon and technical terms that might not be understood. Do not assume that terms familiar to the data scientist are familiar to the recipient.
Consider the needs and perspective of the recipient.
Ask clarifying questions and be specific. Rather than asking “Does this make sense?” ask “Did I convey the difference between statistical and practical significance?”
Do not overload visualizations with unnecessary detail such as chart junk, excessive labeling and annotations. Use presentation graphs for presentations, not exploratory visualizations.
Rely on pre-attentive attributes in visualizations to let the audience understand the contents intuitively, rather than having to think about it.
Use storytelling (Chapter 3).
Do not make the audience read text on slides. Do not read the text on slides yourself.
When using PowerPoint or other slide-making tools, use the assertion–evidence format for slides. A headline-style title provides the assertion of the slide, the important message being conveyed. The remainder of the slide consists of few bullets (if any) and visuals that provide evidence of the assertion.
Avoid “eye charts”. Graphics and tables are not meant to test the visual acuity of the audience.
Limit the number of items the audience has to hold in their head to 3–5.
Consider the person behind the screen: written communication does not benefit from face-to-face contact so choose words wisely—especially when using digital channels such as email, messaging services, social media.
Be mindful of time zones in electronic communication. Nobody wants to see an email at 9:30 pm (or 5:00 am) marked High Importance because you did not remember that you are on a global team.
Use active listening. Try to hear what is being said rather than waiting for your chance or turn to speak (Chapter 10).
Use metaphors, analogies, and similes to explain technical concepts (Chapter 12).
Pay attention. To the audience, to the environment, and to yourself (Chapter 11).
Practice (the individual skills) and rehearse (in a real setting).
Do not Reply All to emails unless that is what you really really need to do. When folks erroneously reply to all recipients do not Reply All to tell them to stop. That is known as the Reply All Apocalypse.
Reply all: Please everyone, stop hitting reply all.

Not unlike the restaurant reservation example, creating communication that is computationally kind to the recipient can increase mental burden for the communicator. We have to spend more time and effort crafting compelling visuals rather than copy-paste from a paper to a slide deck. We have to craft stories rather than reciting facts. We have to practice and rehearse to give an extemporaneous speech.